
WordPress is one of the web’s most popular content management systems, powering nearly one-third of the internet. Although it still has a reputation as a blogging platform, it’s rising as a powerful force in ecommerce too.
Unfortunately, popularity also makes you a prime target for each new cyber attack that comes along.
Although WordPress (WP) is used by Fortune 500 companies, the majority of WP sites are owned by small to medium businesses (SMBs). This is another factor in the number of attacks. In fact, a cyber security report conducted by Symantec Corp shows that cyber attacks on SMB websites more than doubled over a five-year period; they now constitute 43 percent of all hacked websites.
Why hackers love small business websites
The simple fact is, most small business owners are unaware of just how insecure their websites are. Those who do know the danger often don’t have the budget for advanced security.
Apathy plays a role as well.
No one really believes it can happen to them until visitors get tired of running into a buggy (or hacked) site. An ecommerce operation that has enjoyed business growth fueled by positive online reviews can be destroyed just as quickly when one and two star ratings start flooding their page.
Avoid this kind of review decline by understanding the most common reasons for lack of adequate small business security:
- Lack of routine security audits
- Inadequate employee cyber security training and awareness
- Lack of access control, which regulates which users can use which data
- Outdated cyber security software and apps
- No uniform cyber security policy
What kinds of attacks are WP websites at risk for incurring?
The most common cyberattacks are phishing schemes, adware, and credit card skimmers. There’s also a rising threat from ransomware and cryptojacking attacks.
A new ransomware variant called EV ransomware specifically targets vulnerabilities in WP websites. This attack probes for weaknesses and uploads the virus once it has successfully compromised a WP website. Once the EV ransomware is introduced, it’s able to encrypt the site files, locking administrators out until the site owner pays up.
You’ll know that your WP website has been compromised when you attempt to get into your admin panel and meet an interface that looks like this:
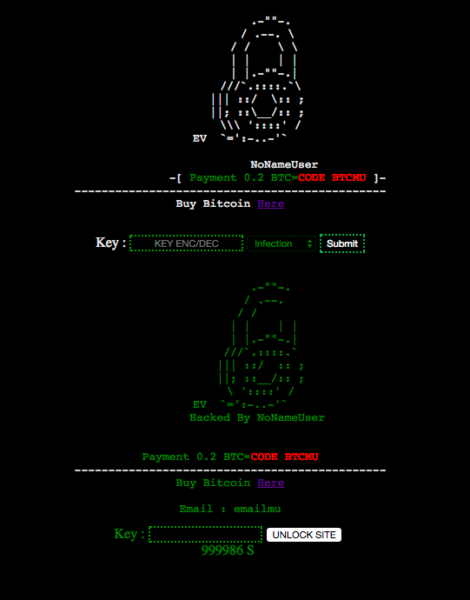
Once an attacker finds a weakness in your system, perhaps due to an outdated plugin or other common mode of entry, such as email attachments, they release a file that begins an encryption process. Within this file is a directory that is supposed to enable a site owner to decode the encryption and unlock their site files once they have paid the ransom and obtain the key. The problem with this particular attack is that there is actually no decryption key.
What to do if you’ve been attacked
Experts advise that those who are victims of an EV ransomware attack should not pay the ransom as there is often no way ever provided to unlock your encrypted files afterwards. Paying the attacker will just result in losing your money with no remedy for the attack.
It may sound hopeless, but there is a way out if you’ve been infected, provided you had the foresight to choose a web hosting provider that conducts regular backups of your site. Most dedicated and cloud hosts perform backups daily and have several layers of redundancy.
Of course you could do the same thing on your own but that apathy bug gets in the way all too often. Regardless, if you have a recent backup of your files somewhere, it’s a fairly simple matter to restore them to your website, after which you should install a firewall to prevent further attacks.
However…
The best cure for an attack is prevention
Even if you’re lucky enough to have a backup to restore your files, you’ve lost time and possibly business trying to regain access to your site. It’s also possible that you’ve tarnished your reputation, and who knows what other shenanigans have occurred in the meantime.
The best way to avoid all of the hassle, embarrassment, and possible financial loss is to keep criminals from accessing your WP website to begin with.
Here are 5 things you should do right away to keep your site secure:
1. Always download from trusted sources.
It takes nothing to set up a domain. In fact, a security report released by Cisco last year states that more than 20 percent of suspicious domains are less than a week old. Take care when opening emails from someone you don’t know, and check the history of any that don’t seem right by dropping the URL into the lookup search box at Whois.
2. Use official platforms.
Because WordPress is an open source platform, there are quite a few unsecure plugins and themes that are tempting to newbies because they’re free. Steer clear of unsupported plugins and themes you’ll find in public collections. Either use the plugins available from the WP plugin directory, which contains free and premium plugins, or purchase a license from a reputable developer that offers continual support, updates, and security patches.
3. Make backups part of your regular routine.
We already mentioned this but it’s important enough to repeat. Even if your hosting company provides system backups as part of your plan, you should also make a habit of performing your own regular backups and placing them in virtual storage.
4. Keep on top of software updates.
One of the main modes of website breaches is through site owners using outdated software, apps, and plugins. Install updated firmware for routers, enable auto scanning for new threats through your anti-virus and anti-malware, install security patches and updates as soon as the become available, and uninstall any old, unsupported, or unused themes and plugins. Don’t simply disable them; that’s just inviting hackers into your system.
5. Install a VPN on all devices and networks.
Virtual private networks allow you to hide your IP address as well as provide end-to-end encryption from your router to your device. Make sure that you install one on each network and device you use, and insist that all employees and vendors do the same. Be sure that the VPN you choose uses the most current DNS leak protection, encryption protocols, and SSL authentication.
Final thoughts
In the two years since the discovery of EV ransomware, millions of new variations on it, as well as a variety of spam and phishing schemes, have been created. While we can never make ourselves 100 percent secure from breaches and cyber theft, increasing awareness among your staff and vendors, in addition to deploying current security best practices, will give you the best odds of warding off attacks.



